Compliance
[<Audit Logs> + <Microsoft 365>]
[Description – < Microsoft 365 – Analyzing Audit Logs>]
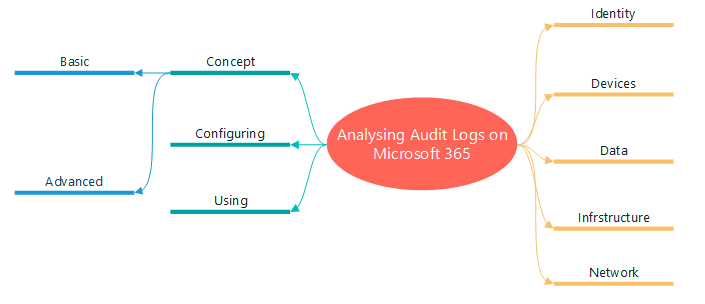
Concept
Audit log search is functionality is turned on by default for Microsoft 365/ Office 365.
Basic
The Basic Audit is available for all non-E5 licenses or guest users in your organization, being that audit records are retained for 90 days.
Advanced
Add functionality to retention policy for all organizations. There is a default policy that retains all Exchange Oline, Sharepoint Online, OneDrive for Business, and Azure Active Directory audit records for one year.
The Advanced Audit required Office 365 E5 or Microsoft 365 E5 license, or Microsoft 365 E5 Compliance or E5 eDiscovery and Audit add-on license.
Permission needs to search the audit log.
- “Compliance Management Administrators” – to assign role to user need access https://security.microsoft.com/ -> Permission & role -> Email & collaboration role -> roles.
- “Organization Management” – to assign role to user need access https://security.microsoft.com/ -> Permission & role -> Email & collaboration role -> roles.
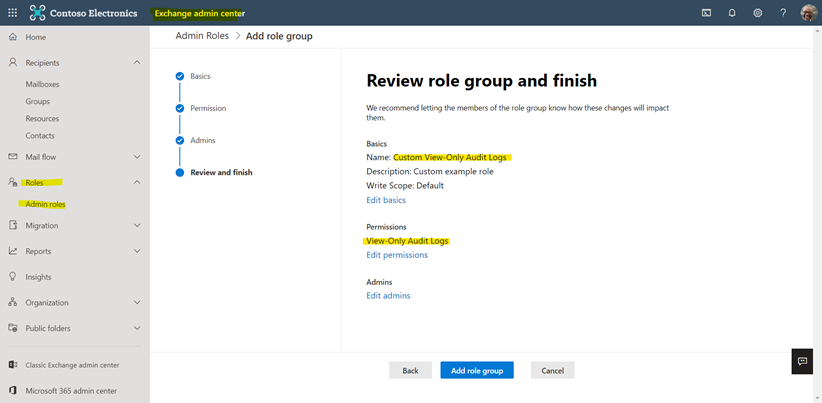
Or create a custom role to search and view Audit Logs on Exchange Admin Center (least privilege concept):
- View-Only Audit Logs role (Exchange admin center Portal)
- Audit Log (Exchange admin center Portal)
Creating a custom role, access Exchange Admin Center (https://admin.exchange.microsoft.com/) -> Roles -> Admin roles -> Add role group.
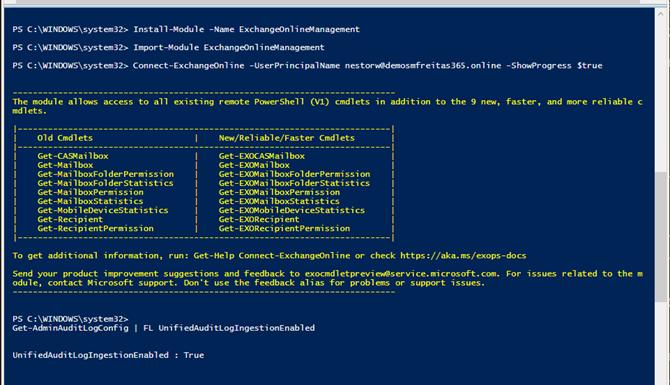
We are verifying if the audit log search is turned on using Powershell.
Example:
{
#Connect to Exchange Online PowerShell
Install-Module
-Name
ExchangeOnlineManagement
#Connect with user MFA
Import-Module
ExchangeOnlineManagement
Connect-ExchangeOnline
-UserPrincipalName
nestorw@demosmfreitas365.online
-ShowProgress
$true
#Check if Audit Log is turn on
Get-AdminAuditLogConfig
|
FL
UnifiedAuditLogIngestionEnabled
}
{
#Turn on Audit Log
Get-AdminAuditLogConfig
|
FL
UnifiedAuditLogIngestionEnabled
#Turn off Audit Log
Set-AdminAuditLogConfig
-UnifiedAuditLogIngestionEnabled
$false
{
How to use Audit Log search
I am visualizing user and administrator activities. Below are types in Microsoft 365.
| Activities Logs from Users and Admins in Microsoft 365 |
Admin activity |
User activity |
| SharePoint Online and OneDrive for Business |
X |
|
| Exchange Online (Exchange mailbox audit logging) |
X |
|
| SharePoint Online |
X |
|
| Azure Active Directory (the directory service for Microsoft 365) |
X |
|
| Exchange Online (Exchange admin audit logging) |
X |
|
| eDiscovery activities in the security and compliance center |
X |
|
| Power BI |
X |
X |
| Microsoft Teams |
X |
X |
| Dynamics 365 |
X |
X |
| Yammer |
X |
X |
| Microsoft Power Automate |
X |
X |
| Microsoft Stream |
X |
X |
| Microsoft Workplace Analytics |
X |
|
| Microsoft Power Apps |
X |
X |
| Microsoft Forms |
X |
X |
| Sensitivity labels for sites that use SharePoint Online or Microsoft Teams |
X |
X |
| Briefing email and MyAnalytics |
X |
X |
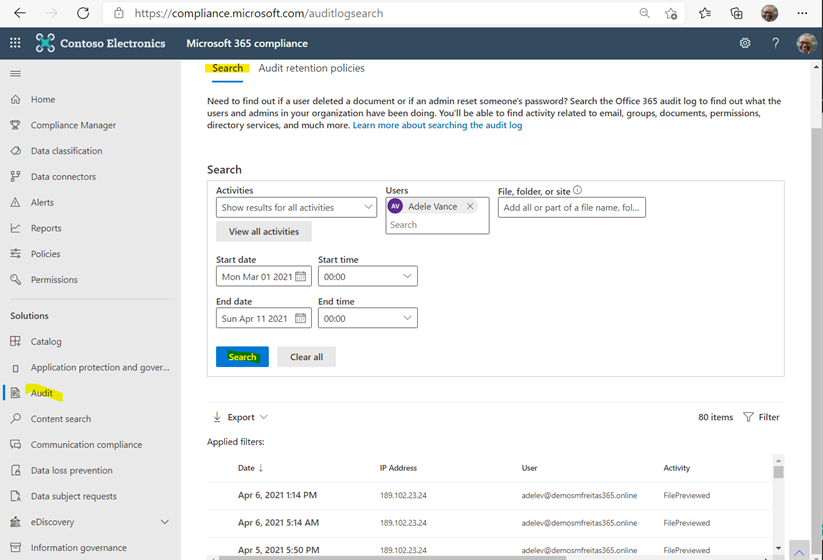
To searching the Audit Log, access Microsoft 365 Compliance (https://protection.office.com) -> Audit -> Search
REFERENCE:
Search the audit log in the compliance center
Get-AdminAuditLogConfig
https://docs.microsoft.com/en-us/powershell/module/exchange/get-adminauditlogconfig?view=exchange-ps